Information System Audit Services
Khandhar Mehta and Shah | Information System Audit

Information System Audit Services
The world of business is very dynamic.
Every company has started to become aware of the need for robust information technology in today’s densely networked business world. Therefore, information technology needs security from both internal and external threats. To safeguard this valuable intellectual property, every company must get the information system audit (IS Audit) done regularly and carefully from experienced IT auditors. As the demand for IS Audit/IT audits is on a surge for them to address the changing requirements and demands of business these days, it is high time you must get your information systems Audit done from our experienced IS auditors.
What is information system audit
Information system audit or information technology audit can be defined as a process of evaluating and collecting evidence from the information technology, operation, and system of the organization to align them with the corporate vision, mission, and goals. It encompasses the evaluation and review of the information processing system, interfaces, and other non-automated processes of an organization.
KMS adopts a risk-based audit approach and performs a thorough risk assessment before starting with the information system audit. A risk-based IS auditing approach allows our IT auditors to decide the degree of reliance they can place on internal controls while performing their information technology audit.
Scope of information system audit
The scope of IT audit depends on the nature and size of the business. Ideally, it encompasses all the IT resources, including hardware, software, networking, plans, policies, procedures, and systems. IS Audit is generally performed on a yearly basis.
During the course of an information system audit, we test physical security controls and then go on to test logical security controls, network security, disaster recovery procedures, and business continuity plans. We then undertake data integrity assessment, assessment of controls over network, database, applications, and IT infrastructure. We review the IT strategy, organizational structure, and IT service process, including support function, service management, etc.
Being one of the well established CA firms in Ahmedabad, we always focus on giving our clients the best in class services that reflect our values and vision of transparency, flawless, and professional work. Visit our CA website to understand and know more about our services and our company. Choose us for your business as the best deserves the best.
Information system audit procedures
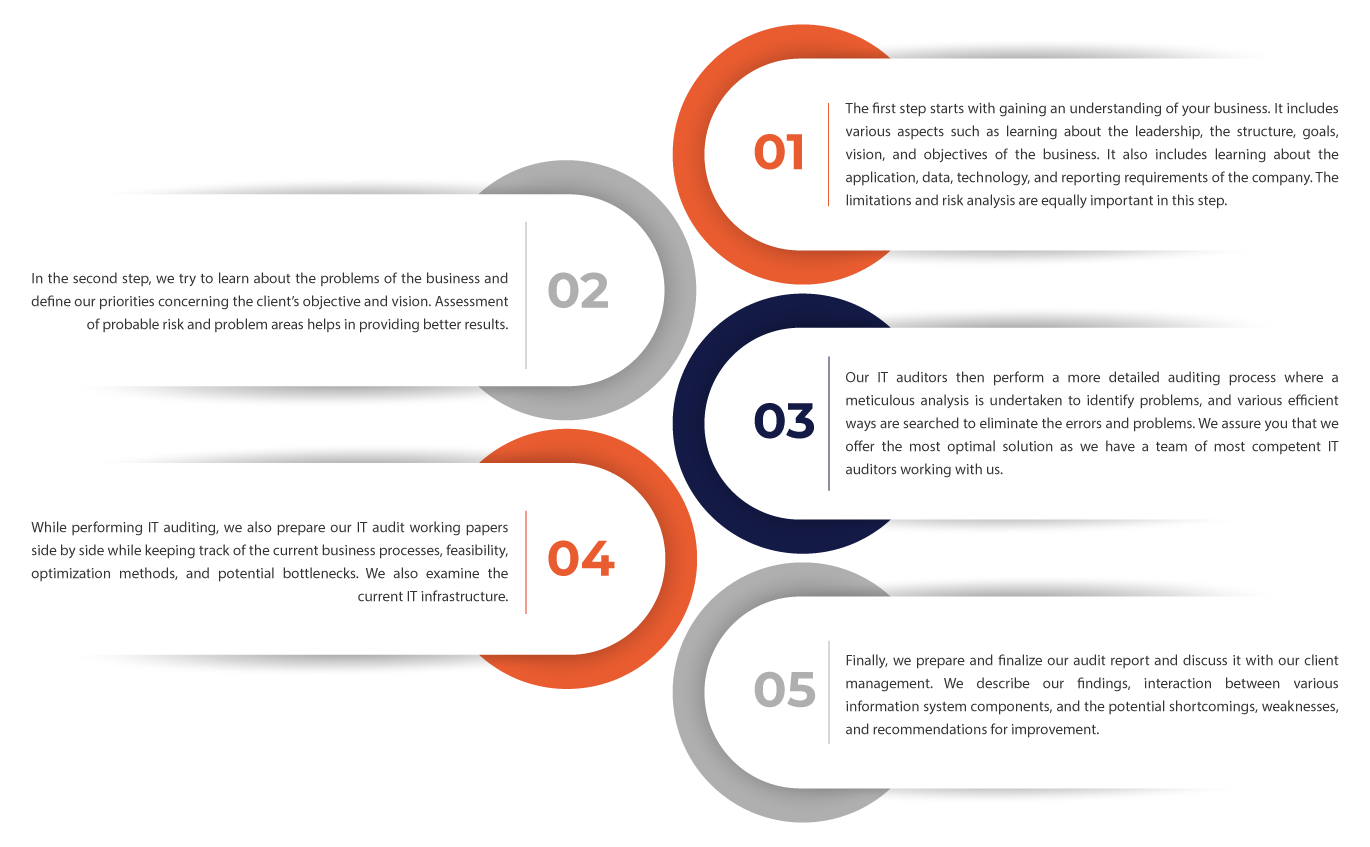
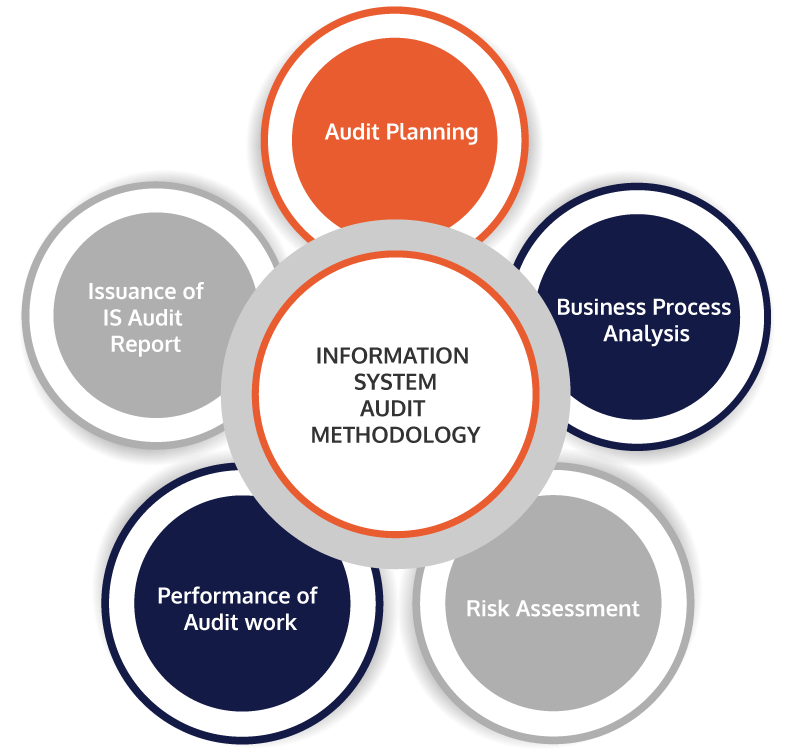
Information System Audit Methodology
Importance of information technology audit

IT audit reduces the risk related to IT infrastructure
The risks associated with confidentiality and availability of various IT processes and structures are protected, and risks are mitigated by conducting an IT audit. An information system audit also helps in improving the efficiency and effectiveness and reliability of the IT system by assessing and covering a wide range of threats in the organization. It gives the company a clearer vision for the course of action concerning the outcomes of the audit.

Enhances IT
governance
One of the most critical functions ensured by IT audit is making sure that all the laws, compliances, and regulations are met by the IT department and the employees of the company. It improves governance and also helps the management understand the risks and control of the firm’s technological environment.

Enhancing the security
of data
After assessing the risk and errors, an IT audit can also evaluate and identify the solutions. It allows the organization to reconstruct and redesigns the poorly designed or ineffective control system leading to the improvement of IT control. As at KMS, we use an advanced set of tools and technologies to carry out auditing. We are capable of detecting both internal and external threats and immediately take the required course of action to solve them.
Objectives of IT audit
What can you expect from an IT audit?

The IT audit report prepared by our auditors has a detailed description of the current scenario of the IT architecture, and IT process followed by the company. It serves as the base document when the organization is planning for an IT infrastructure upgrade.

We provide detailed recommendations for the optimization of IT infrastructure, IT processes, and IT architecture in your company. The net result is, you have reliable IT risk management capability.
It results in significant cost savings and improved data availability and integrity as a result of better IT governance.

We provide a roadmap for improvements, development, and implementation of business applications with respect to our findings from the IT audit.

An information system audit ensures compliance with the regulatory requirements and latest information security standards.
key features of KMS for IS audit?
Our auditing methodology includes planning, document review, situation, and risk identification. We examine the alignment of your IT structure with your business requirements and make sure they comply with the rules, regulations, policies, and procedures.
What does our client think about us?
trust. transparency. professional expertise.


